Simulators
Regarding Security
Despite the options available here, in this section; the idea is to be updated to be ready for what is coming up.
And all different of security levels will need to be verified.
Source
These possibilities were provided by Cyber Gurus and Red Zone
Hope you enjoy the content and curb your enthusiasm
Simulators
Creating a real situation with no impacts
One of the biggest challenges today is to ensure that your investment was made in the right places with the right equipment and applications through trained and experienced professionals without causing greater damage to your networks, dependencies and business. Your brand should be protected, but scan simple tests and pentests alone won't really show the holistic view of your entire investment and ensure that your company is safe. Therefore, Cyber Gurus, a company in our group, offers manual and automated options so that your whole company, security policies (internal and external with its processes and procedures) and its professionals (including partners and 3rd. party) can be evaluated completely, correctly and with total confidentiality. For all this, here are the options offered:
1. Executive War-Room Simulation

Coverage: All Platforms & Executive Board
Focus: Decision-Make, Performance, Brand Protection, Policies & Communication
– The most of attacks from 2024 were based on lack of knowledge about information security, old vulnerabilities and not updated/upgraded assets. The Executive Board needs a different approach to handle bad situations with a minimum knowledge about the current status of your company regarding cybersecurity and its requires decisions from different levels and not only of CISO's desk. Cyber gurus are able to bring the outside real world to inside, to a War-Room where the decisions will be taken, offering different scenarios to simulate impacts to Brand, Executive Board, Individual Director or Area, prejudices, fees, press situation, laws and much more.
2. Technical Table-Top Simulation

3. Cymulate
2. Technical Table-Top Simulation

Coverage: All Platforms, Professionals & Areas
Focus: Elapsed Time, Decision-Make, Validate Policies, Communication Among Areas, Resilience, Disaster Recovery
– The technical core must be involved but not only them. Different areas must be available and work together to solve Ransomware, Phishing and others attacks and outages caused by different vectors with multi-case impacts facing real bad situations simulated with all professionals participating during a day event. The exercise will provide a real map of gaps and lack of information by areas or different professionals. Perfect cases to evaluate the security maturity of all involved.
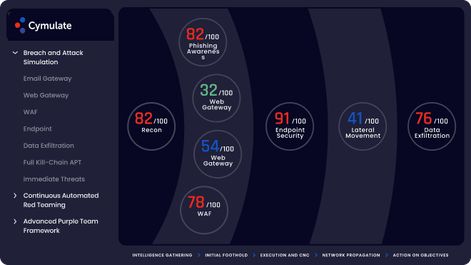
3. Cymulate

Coverage: Automated Ransomware Simulation
Focus: Breaches, Email, WAF, End-Point, Data Exfiltration, WEB, APTs, Lateral Movements, Infrastructures, etc.– Cymutale is a partnership that offers a tool to simulate different automated attacks. This is a software that needs a high security professional knowledge to produce the coverage tests of whole scope and available assets, whit no impacts to these environments and, at the end; different reports will be created showing what was impacted and why it happened. This will be able to evaluate all different layers of protection against different attacks. Contact the Cyber Gurus for more details and legal possibilities.
4. KnowBe4
4. KnowBe4

Coverage: Automated Phishing Simulation
Focus: Education & Phishing Approaches.
– KnowBe4 is another partnership that offers different tools to simulate phishing attacks and provide more material for professional education. They offer different software to validate the security level of your professionals regarding data and email security and all results are presented in different dashboards during the contract. Contact the Cyber Gurus for more details and legal possibilities.
Remember, Cyber Gurus offers other methodologies, other options, tests and pentests, assurance coverage, manual and automated simulators with different approaches that fits most of all branches of security market and their needs. So contact them to check it all.
